Eng
Eng
- Home Appliances, Tools and Household Goods
- Consumer Goods & Electronics
- Products & Solutions for Enterprises
- Toys & Goods for Kids
- All vendors
- Home Appliances, Tools and Household Goods
- Consumer Goods & Electronics
- Products & Solutions for Enterprises
- Toys & Goods for Kids
- Blowers
- Lawn mowers
- Garden shredders
- Cultivators and motoblocks
- High-pressure cleaners
- Chain saws
- Accessories for irrigation and high pressure cleaners
- Pumps
- Shears for garden
- Sprayers
- Shovels
- Garden tools
- Garden furniture
- Garden fencing
- Potbelly stoves
- Trolleys for garden construction
- Tenty i zavisy
- Goods for picnic
- Accessories for lawn mowers and trimmers
- Accessories for chainsaws
- Wood splitters
- UPS and accessories
- Sources of uninterruptible power supply
- Gaming products
- Gaming PCs and hardware
- Processors for gaming
- Game consoles and accessories
- Virtual reality glasses
- Gaming peripherals and accessories
- Glasses for computer
- Games
- Game collectible figurines and accessories
- Merchandise, gaming attributes
- Computer peripherals
- Computer components
- Media tablets
- Monitors
- Drives and Flash-memory
- Laptops & Accessories
- PC and All-in-One PC
- Software
- Accessories and options for computer and office electronics
- Cleaners
- 2E Custom PC
- Computer tables
- Travel goods
- Cooler bags, thermoboxes
- Gas cylinders and accessories
- Haberdashery
- Umbrellas
- Tactical gear and equipment
- Radio equipment and navigation
- Tactical watches
- Accessories for tactical drones
- Tactical equipment
- Pouches
- Military gloves
- Knee and elbow pads
- Plate carriers
- Elements for plate carriers
- Tactical vests
- Tactical flask
- Tactical eye protection
- Tactical glasses
- Tactical goggless
- Personal heating equipment
- Chemical heating
- Electric heating
- Hearing protection
- Active Shooting Headphones and Headsets
- Navushnyky ta harnitury striletski pasyvni
- Tactical shovels
- Backpacks, bags, duffle-bags
- Tactical backpacks
- Backpacks, bags, duffle-bags
- Sling bags
- Camping equipment
- Karrimat and mattresses
- Tactical clothing and footwear
- Raincoats
- Chemical light
- Bicycle accessories
- CCTV Cameras
- Smart switches and buttons
- Smart Sensors
- Smart controllers, gateways, panels
- Smart sockets, relays and motors
- Smart drives, thermostats, control panels
- Smart sirens
- Search engines
- Heating systems
- Towel warmers
- Radiators
- Pipe fittings
- Accessories for radiators and heated towel rails
- Accessories and components for hot water heating
- Circulation pumps
- Underfloor heating hydronic
- Underfloor heating
- Underfloor heating pipes
- Intercom systems
- Thermoregulators
- Sewer pipes and fittings
- Accessories and mounts for alarm systems
- Accessories for temperature controllers
- Accessories for thermotechnics
- Control automation for thermotechnics
- Quick installation systems
- Network filters
- Light source, Lights
- Accessories for lamps
- Chandeliers, lamps, sconces, floor lamps
- Electric light bulbs
- Light fixtures
- Fixtures external
- Indoor (interior) light fixtures
- Fitting and light accessories
- Electrical-installation equipment
- Sockets and switches
- Electrical switchboards
- Contactors
- Terminals
- Automatic switches
- Circuit breakers
- Voltage Limiters
- Relays and alarms
- Tires
- Modular and change-over switches
- Kits and accessories for smart lighting
- Clockwork toys
- Toys-keychains
- Toys
- Bath toys
- Toys for sand
- Playing Kits
- Toy transport
- Toy weapons
- Game Figures and Accessories
- Construction sets
- Dolls
- Puppet show
- Doll accessories
- Baby mobiles
- Musical instruments
- Stuffed Toys
- Balls
- Board games
- Puzzles
- Вeanbag
- Radio-controlled cars
- Learning toys
- Creativity
- Goods for holidays
- Music and storage boxes
Security tools in the database management system (DBMS) MySQL Enterprise Edition

In a world where the number of cyber threats is constantly increasing, the protection and security of confidential information from unauthorized access and cyber-attacks becomes a critical task for business continuity, maintaining reputation and financial stability.
Therefore, MySQL Enterprise Edition has the following data security features:
- Enterprise Autentification: external authentication modules
- Enterprise Encryption: public/private key cryptography, asymmetric encryption
- Enterprise Transparent Data Encryption (TDE): 256 AES encryption, key management
- Enterprise Masking and De-identification: de-identification, anonymization of confidential data
- Enterprise Firewall: blocking SQL injection attacks, intrusion detection
- Enterprise Audit: audit of user activity, compliance with regulatory requirements
MySQL Enterprise Authentication
MySQL Enterprise Edition is ready to use external authentication modules for easy integration with existing security infrastructures, including Linux Pluggable Authentication Modules (PAM) and Windows Active Directory authentication modules. By authenticating MySQL users from centralized directories, organizations can implement single sign-on. It is possible to use the same usernames, passwords and permissions. This makes MySQL administrators more productive by eliminating the need to manage credentials on separate systems. It also helps to make the IT infrastructure more secure by leveraging existing security rules and processes (such as identifying weak passwords and managing password expiration).
MySQL Enterprise Encryption
To protect sensitive data throughout its lifecycle, MySQL Enterprise Encryption provides industry-standard functionality for asymmetric encryption (public key cryptography). MySQL Enterprise Encryption provides encryption, key generation, digital signatures, and other cryptographic functions to help organizations protect sensitive data and meet regulatory requirements.
MySQL Enterprise Encryption enables:
- Protect data using a combination of public, private and symmetric keys to encrypt and decrypt data.
- Encrypt data stored in MySQL using RSA, DSA or DH encryption algorithms.
- Add a digital signature to messages to confirm the authenticity of the sender (non-repudiation) and the integrity of the message.
- Eliminate unnecessary data access by enabling database administrators to manage encrypted data.
- Interoperate with other cryptographic systems and devices without changing existing programs.
- Avoid exposing asymmetric keys in client programs or on disk.
MySQL Enterprise Transparent Database Encryption
MySQL Enterprise Transparent Data Encryption (TDE) protects sensitive data by encrypting data at rest in the MySQL Enterprise Edition database. This option protects information privacy, prevents data leakage, and helps meet regulatory requirements:
- General Data Protection Regulation (GDPR)
- Payment Card Industry Data Security Standard (PCI DSS)
- Health Insurance Portability and Accountability Act (HIPAA) and others
MySQL Enterprise TDE provides data encryption at rest by encrypting physical database files using standard AES algorithms. Data is automatically encrypted in real-time before writing to storage and decrypted when reading from storage. As a result, hackers and attackers cannot read sensitive data directly from database files.
MySQL Enterprise TDE has a two-tier encryption key architecture consisting of a master encryption key and tablespace keys, which provides easy key management and rotation. Tablespace keys are managed automatically through secure protocols, and the master encryption key is stored in a centralized key management solution.
Database table encryption and decryption is accomplished without any additional coding or schema modifications. In addition, users and applications continue to access data transparently.
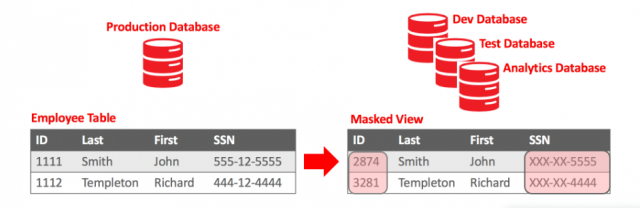
MySQL Enterprise Masking and De-Identification
MySQL Enterprise Masking and De-identification provides MySQL Enterprise Edition users with an easy-to-use built-in solution that helps protect sensitive data from unauthorized use by masking and replacing real values with substitutes.
Masking and de-identification in MySQL Enterprise Edition allows:
- Comply with regulatory requirements and data privacy laws such as GDPR, PCI DSS and others that require de-identification of data.
- Significantly reduce the risk of data leakage by preventing unauthorized access to sensitive dat.
- Protect confidential information by improving development, testing and analytics environments.
Data masking in MySQL Enterprise Edition is implemented on the MySQL Server itself, so the masking logic is centralized and has minimal impact on performance.
Masking and de-identification in MySQL Enterprise Edition can hide or mask sensitive data by controlling how the data is displayed. The functionality includes robust masking algorithms, including selective masking, obfuscation, random data replacement, and other special techniques for credit card numbers, invoices, and other personal information, allowing IT departments to maintain structured rules for de-identifying values. MySQL Enterprise's masking and de-identification features include:
- Selective masking - hides a specific part of numbers or strings, such as phone numbers and payment card numbers.
- Random data replacement – replacing real values with random ones while maintaining format consistency.
- lurring - adding random variance to existing values, such as randomized numerical ranges for salaries.
- Substitution in the dictionary – random replacement of values from dictionaries for certain tasks.
- Blacklist and replacement – replacing the data contained in the blacklist and leaving the data and the data not included in the blacklist unchanged.
MySQL Enterprise Firewall
MySQL Enterprise Firewall option protects against cyber-attack threats by providing real-time protection. Any application that enters user data, such as login fields and personal information, is at risk. Database attacks come not only from applications, but from many other sources, including SQL virus attacks or misuse by employees.
MySQL Enterprise Firewall protects MySQL Enterprise Edition data by monitoring, warning, and blocking unauthorized database activity without any application changes. MySQL Enterprise Firewall provides multiple modes of operation to help administrators block, detect, and respond to malicious database attacks:
- Allow – SQL statements are executed and results are generated for statements that match the approved whitelist
- Block – execution of SQL statements that do not match the approved whitelist is blocked
- Detect – SQL statements that do not match the whitelist are executed and administrators are notified of policy violations
MySQL Enterprise Firewall blocks SQL-Injection attacks that can lead to the loss of valuable personal and financial data. Whitelisting, real-time threat monitoring, SQL statement blocking, and alerts allow DBAs to protect data assets.
MySQL Enterprise Firewall monitors database threats in real time. All incoming queries are passed through the SQL parsing engine and mapped against an approved whitelist of expected SQL statements. SQL attacks are blocked if they do not represent the expected statements.
Assertions that do not match the approved whitelist are blocked, logged, and can be analyzed to help block a potential SQL injection attack. This provides database administrators with valuable information to prevent malicious attacks, credential theft, and data loss.
MySQL Enterprise Audit
In order to comply with regulatory requirements in the medical, financial, government and other sectors regarding the processing and storage of personal data, logging, archiving and on-demand access to audit logs that store data on viewing and working with the most sensitive data are mandatory and acted with them.
MySQL Enterprise Audit provides an easy-to-use auditing solution that helps implement more effective security controls and meet regulatory requirements.
MySQL Enterprise Audit provides database administrators with the tools they need to add auditing requirements:
- User definition of special audit log events - the ability to add custom events to the MySQL audit log, providing additional information related to SQL calls. For example, tracking numbers, support ticket links, or other application context.
- Encryption – audit files can now be encrypted using the AES-256 standard. These files can be served and decrypted by external programs that have the encryption key.
- Compliance with standards and regulatory requirements - providing the data your organization and auditors need for compliance.
- Easy integration with repositories and audit repositories - easy archiving and analysis of XML-based audit logs using Oracle Audit Vault and other third-party solutions, including Splunk.
- Dynamics and ease of management - dynamically enable and disable the audit stream, change filters without downtime.
- Low overhead costs – collecting critical audit data without impacting performance, using fine-grained filtering to minimize audit log size and I/O impact.
- Achieving security goals through a comprehensive audit – the ability to verify the activity of database administrators, prove the authenticity of data and conduct analysis for investigation or discovery.
- Removal of sensitive data and filtering for data security – removing sensitive data from SQL reports in the audit log, filtering by connections, users, table access, access type, operator status (success/failure), query content, etc.
All the above-mentioned security options in MySQL Enterprise make the infrastructure of this database protected and compliant with modern security regulatory requirements.
For all questions about Oracle products, please contact oracle@erc.ua